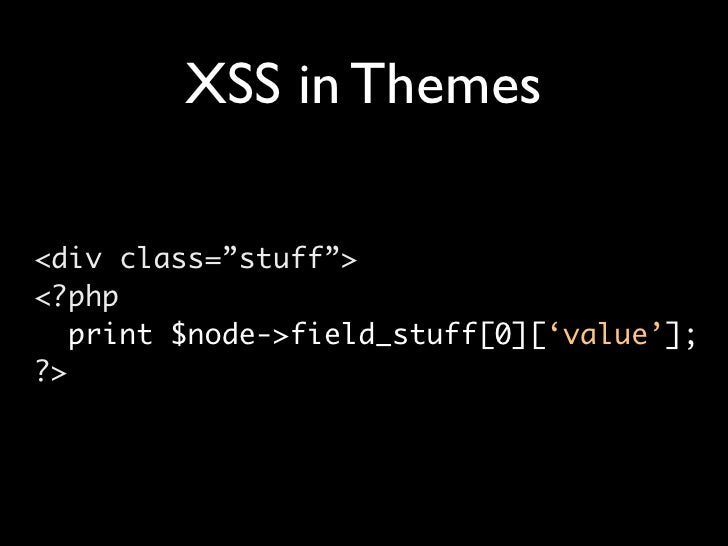
Shop Admin Hacking Tutorial Site
Websites are used daily by a large part of the world's population to carry sensitive data from a person to an entity with online-based presence. In websites containing materials that are shown after authentication only, forms transfer data containing user credentials to server-side scripts. Users store their credit. Aug 22, 2017. Hacking VP-ASP SHOP. I hope you will see whenever you try to buy some thing on the internet with Credit Card (CC), they will show you a very secure, well programmed form. They are carts, like vp-asp xcarts. Specific sites are not hacked, but carts are hacked-able. Below I will be posting a tutorial on how.

Welcome back, my greenhorn hackers! Download Gandalf Exploit. In a, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database. As, the open source database now owned by Oracle, is probably the most widely used back-end database of online websites, we'll use it as an example.
Similar techniques can be used for Microsoft's SQL Server, Oracle, DB2, Postgresql, etc. Hacking Databases with Sqlmap We will be using, once again, which is a versatile and powerful tool for hacking databases. It has been used in a number of successful and highly publicized hacks by Anonymous members and other hackers against web-based databases. Any self-respecting (and for that matter, self-loathing) hacker should be familiar with sqlmap. As such, I want to spend a few tutorials showing you its power and capabilities.
Here we will focus on exfiltration, but it can do so much more. Extracting Data with Sqlmap In this tutorial, we'll work on how to extract the data after we've found the database and enumerated the database. Since the data in the database server is the hacker's 'Golden Fleece,' the ability to find and extract it is among the most critical skills for an effective hacker.
Step 1: Fire Up Sqlmap in BackTrack Let's open up sqlmap in and look at the help screen by typing: •./sqlmap.py -h If you need help finding sqlmap, refer back to. As we can see, the capabilities and options for using sqlmap are numerous. In, we had used a URL to target the database by using the -u switch (such as./sqlmap.py -u '), but notice that in the screenshot above we have the option to do a lot more. We can use a direct connect (-d), the logfile (-l), a bulkfile (-m), HTTP requests (-r), use googledorks (-g), or use a configuration.ini file (-c). For now, we will continue to use the URL option, or -u option, in our attack here, but we will explore the other attack options in future guides. If we scroll down the help screen a bit, we will see another section called 'Enumeration.' These are the options available to enumerate various objects in the target database.